GoldFactory’s Banking Trojan Campaign: Targeting Southeast Asia’s Financial Sector
- Syafiq S

- Dec 5, 2025
- 4 min read

Introduction
In December 2025, the cybercrime group known as GoldFactory launched a widespread malware campaign targeting financial institutions across Southeast Asia. The group’s main weapon is a modified version of banking Trojan malware which infected thousands of mobile users in countries like Indonesia, Thailand, and Vietnam. The malware was cleverly disguised as legitimate banking apps, making it difficult for users to identify the threats. This article explores the background of the GoldFactory campaign, its impact on victims, and offers recommendations for safeguarding against similar attacks in the future.
Attack Background: A Persistent Threat
GoldFactory’s campaign is a continuation of the group's established tactics, leveraging advanced Android banking Trojans like GoldDigger and its more sophisticated variants, including GoldDiggerPlus and GoldPickaxe. These Trojans are embedded within counterfeit banking apps that look indistinguishable from real financial services applications. Users are tricked into downloading these apps, often through phishing messages or calls impersonating government agencies or trusted companies.
Once installed, the malware secretly collects sensitive data such as login credentials, bank account details, and even biometric information. This is done through advanced features like keylogging, real-time screen monitoring, and the injection of fake screens mimicking official system prompts. The malware can bypass security measures by using dynamic code injection methods, allowing it to remain undetected for extended periods.
The Attack Details: How GoldFactory Operates
GoldFactory’s malware primarily targets Android users in Southeast Asia, where it has successfully infiltrated thousands of devices. The campaign begins with fraudulent mobile app downloads. These malicious apps appear to be legitimate banking or payment apps but are actually designed to steal users' personal and financial data.
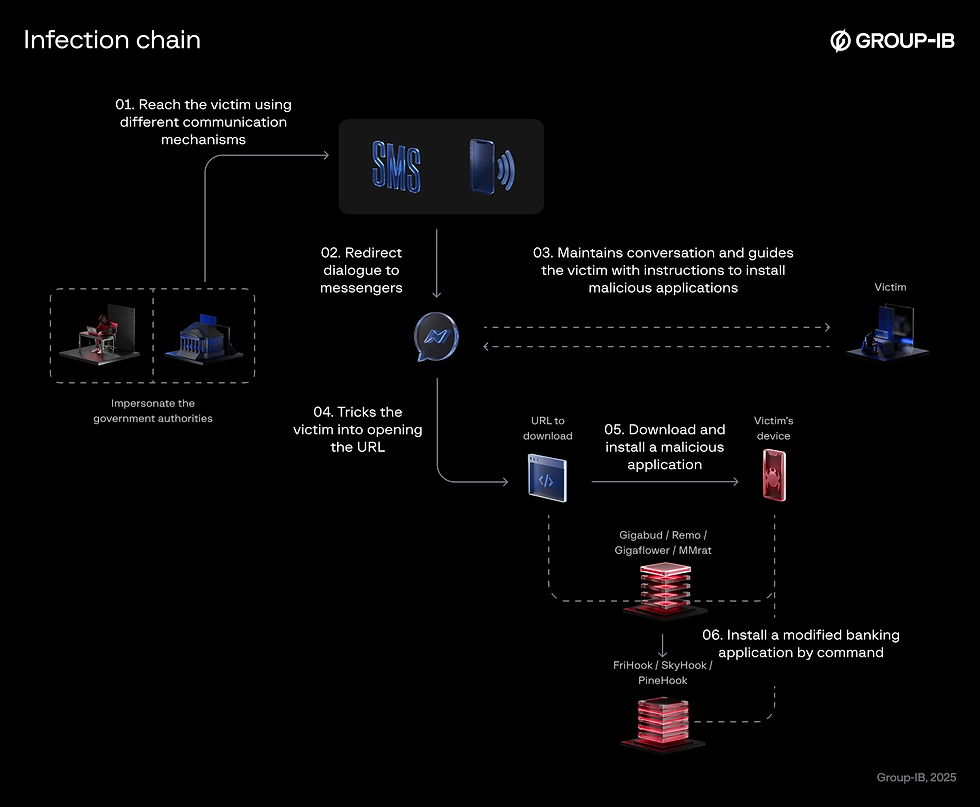
The malware operates by intercepting traffic between the victim and their bank’s servers, allowing attackers to steal credentials, initiate unauthorized transactions, and even bypass two-factor authentication (2FA) in some cases. GoldFactory has also been known to exploit vulnerabilities in app security protocols to give attackers full access to infected devices.
One of the key elements of GoldFactory's success is its ability to target specific geographic regions by using localized content and phishing methods that appeal to the target market. Additionally, the malware is adaptable, able to hide from antivirus detection and continuously evolve its tactics to evade law enforcement and cybersecurity efforts.
Impact of the Attack: Widespread Consequences
The GoldFactory campaign has had far-reaching effects on both individuals and financial institutions. Here are the major impacts:
Financial Losses: Thousands of users have reported unauthorized transactions, with some victims losing significant amounts of money. The malware’s ability to bypass security features has left many unaware of the breach until funds have been stolen.
Reputational Damage: Banks and financial services providers in Southeast Asia have suffered reputational harm as a result of these breaches. Trust in mobile banking systems has been eroded, with many users expressing concerns about the safety of digital banking apps.
Operational Disruption: Financial institutions have been forced to scramble to patch vulnerabilities and protect their networks from further breaches. The ongoing threat has disrupted day-to-day operations, leading to delayed services, financial recovery efforts, and increased pressure on cybersecurity teams.
Rise in Awareness of Cybersecurity Risks: The attack has heightened awareness about mobile app security and the importance of securing personal devices against cyber threats. It has also prompted discussions within the cybersecurity community about the role of weak app security in enabling large-scale financial fraud.
Mitigation Strategies: Strengthening Defenses
While GoldFactory’s campaign has shown the potential for devastating financial impacts, there are several proactive steps that organizations and individuals can take to protect against such threats in the future:
Enforce Strong Authentication: Financial institutions should implement multi-factor authentication (MFA) and encourage users to enable biometric security features, such as fingerprint or facial recognition, for an added layer of protection.
Educate Users About Phishing: Raise awareness about phishing attacks that distribute fake banking apps. Users should be advised to only download apps from official app stores and be cautious of unsolicited links or phone calls from unknown sources.
Secure Mobile Devices: Ensure that mobile devices are protected by strong passwords and encryption. Regular software updates should be installed to patch known vulnerabilities and prevent malware from exploiting outdated systems.
Utilize DDoS Protection Services: For financial institutions, deploying DDoS protection services can help mitigate the impact of volumetric attacks that aim to overwhelm and disable networks.
Implement Endpoint Detection and Response (EDR): Financial institutions should use EDR solutions to monitor for abnormal behavior on mobile devices, enabling quick detection and response to potential threats.
Collaboration with Law Enforcement and Cybersecurity Firms: Institutions should work closely with law enforcement and cybersecurity firms to monitor suspicious activities, share threat intelligence, and collaborate on takedown efforts to disrupt malware distribution.
Conclusion: A Call to Action for Mobile Banking Security
The GoldFactory campaign underscores the vulnerabilities that still exist within the financial sector, especially in the mobile banking space. As cybercriminals continue to evolve their tactics, financial institutions must prioritize securing mobile platforms and educate users about the risks of downloading malicious apps.
By adopting stronger security practices, keeping software up-to-date, and fostering a culture of awareness, financial institutions can better safeguard their users and reduce the risks posed by malware attacks like GoldFactory.
Reference
https://thehackernews.com/2024/02/chinese-hackers-using-deepfakes-in.html https://thehackernews.com/2023/08/gigabud-rat-android-banking-malware.html https://github.com/canyie/pine https://github.com/jmpews/Dobby https://dti.domaintools.com/banker-trojan-targeting-indonesian-and-vietnamese-android-users/ https://frida.re/docs/gadget/




Comments